Identity Resources
What are identity resources and how one would use them to create requests using the scope parameter.
Identity Resources, they are a named group of claims about a user that can be requested using the scope parameter. The OpenID Connect specification suggests a couple of standard scope names to claim type mappings that might be useful to you for inspiration, but you can freely design them yourself.
The OpenID scope, however, is mandatory as it informs the provider to return the sub (subject id) claim in the identity token.
The Identity Resources Table will contain the available resources when checking the Identity Resources section.
Create a New Identity Resource by clicking the New Identity Resource button. On the Identity Resource Form one must input the required information to create the Identity Resource.
The first three items include the Name, Display Name, and the Description of the Identity Resource.

In the Name field, input a unique name for this Identity Resource.
This would be the value the client would have to use for the scope parameter in the authorized request.
In the Display Name field, input the information that would be used, for example, in the consent screen. Then, in the Description field input information regarding that specific Identity Resource.
Once done one can modify the behavior using the options below.
Show In Discovery Document will specify whether this scope is shown in the discovery document when turned on. The default value of it is set to true.
The Required toggle switch specifies whether the user can unselect the scope on the consent screen when turned on. The default value of it is set to false.
The Enable toggle switch, when turned on, will indicate if this resource is enabled and can be requested. The default value is set to true.

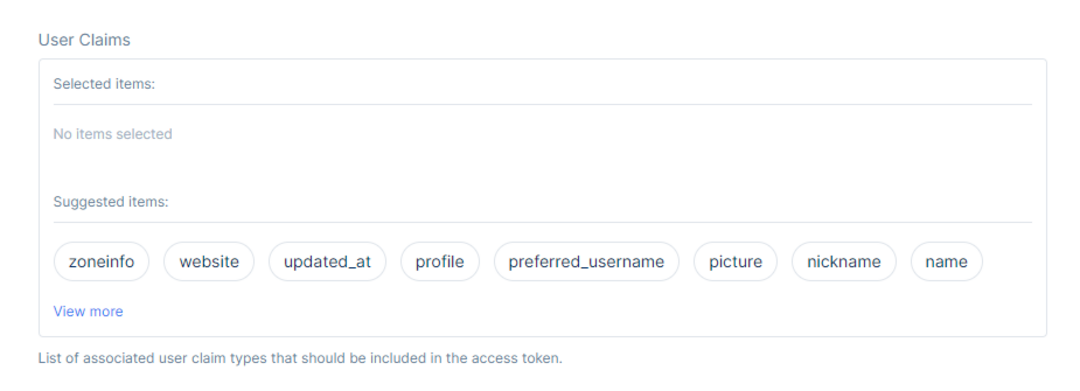
The User Claims section lists associated user claim types that should be included in the access token.
Once done with the information, click the Save button to save the changes or Cancel to discard the changes. On Save, the new Identity Resource will be added to the Identity Resources List View.

Finally, there is also the option to Manage Identity Resource Properties and Delete Identity Resource in the Sensitive Actions section.
To Manage Identity Resources Property, click Manage Identity Resources Property.

Any custom API Resource specific values can be held here as needed.

In the Sensitive Actions section, you will be given the option to delete the specific Identity Resource. Deleting the Identity Resource will not allow the application to request the group of claims selected. This action cannot be undone.