Security
Porta can detect a variety of attacks and stop malicious attempts to access your applications.
In the Porta Dashboard, you can enable the following attack protection options to mitigate attacks:
Bot Detection
Suspicious IP Throttling
Brute Force Protection
Breached Password Detection
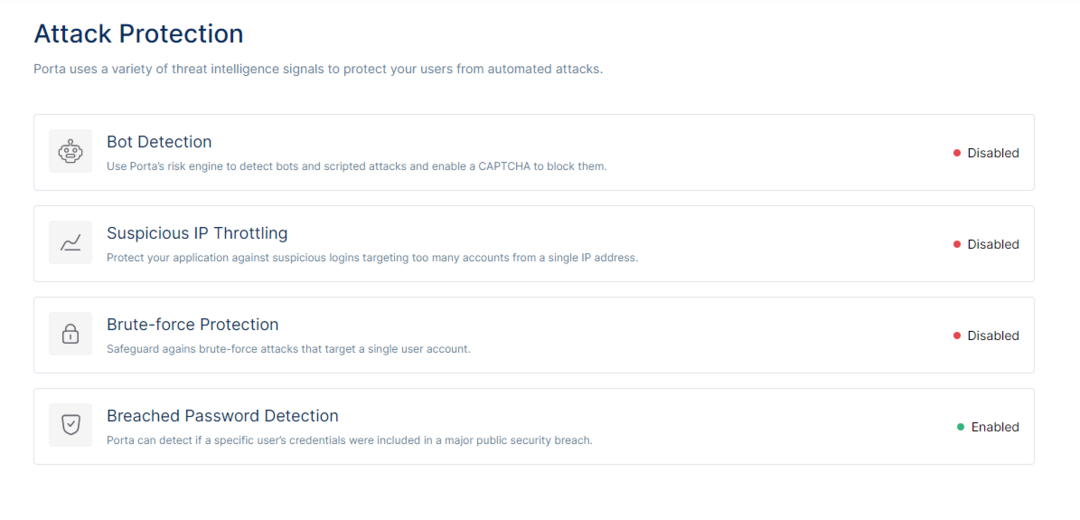
An overview of the attack protection options Porta offers
How it Works
When it comes to combating abuse, there is no silver bullet. Porta uses various threat intelligence signals to protect users from automated or manual attacks.
Bot Detection
Bot Detection triggers a CAPTCHA step when a login attempt comes from an IP suspected to be used by a Bot. The risk signal consists of IP reputation computed by analyzing the quality of traffic seen by each IP. Bot Detection poses little friction to legitimate users, where if a risk is detected, a CAPTCHA step is displayed in the login experience to mitigate against bot and scripted traffic.
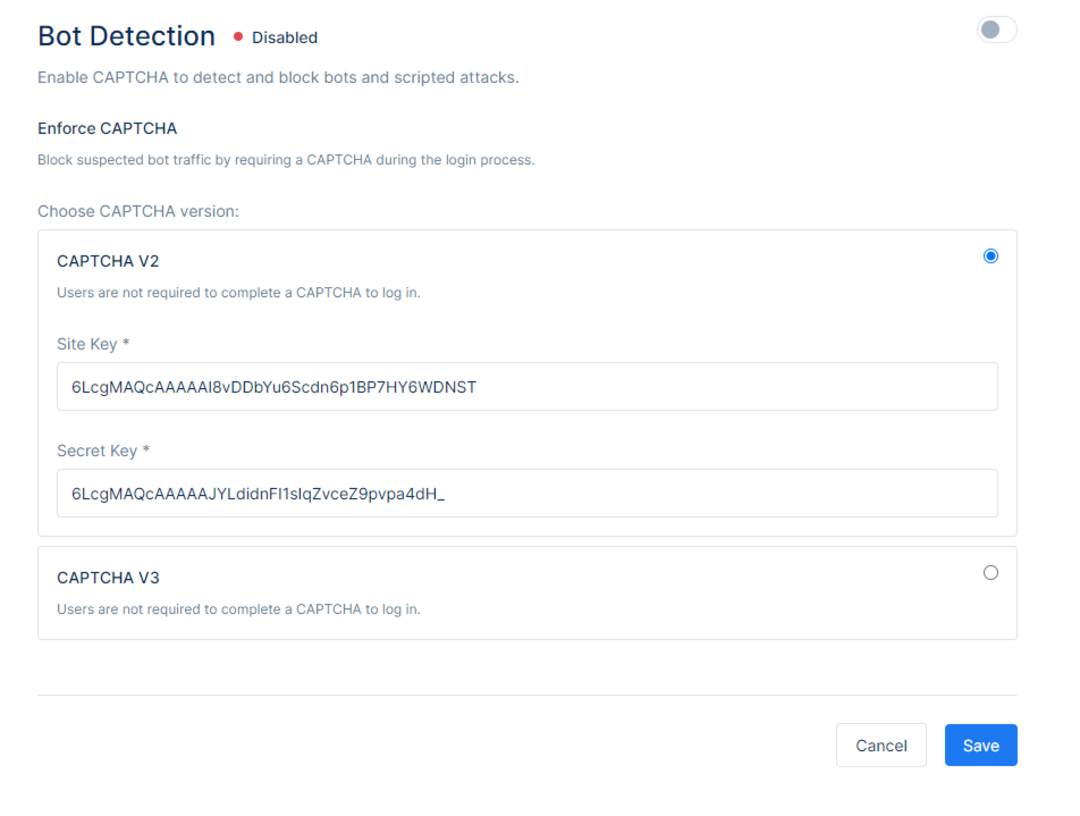
Depending on the preferred choice, choose between the CAPTCHA V2 or CAPTCHA V3 service, and provide a Site Key and a Secret Key.
To start using reCAPTCHA, you need to sign up for an API key pair for your site at Google reCAPTCHA. The key pair consists of a site key and secret key. The site key is used to invoke reCAPTCHA service on your site. The secret key authorizes communication between your application backend and the reCAPTCHA server to verify the user's response. The secret key needs to be kept safe for security purposes.
Choosing the type of reCAPTCHA
There are two types of reCAPTCHA to choose from when enabling it.
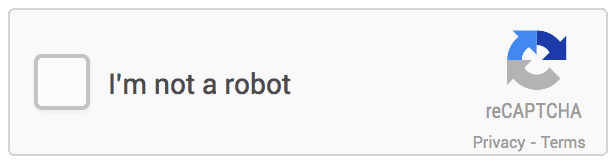
reCAPTCHA v2
The "I'm not a robot" Checkbox requires the user to click a checkbox indicating the user is not a robot. This will either pass the user immediately (with No CAPTCHA) or challenge them to validate whether or not they are human by an image recognition challenge.
reCAPTCHA v3
The reCAPTCHA v3 does not require the user to click on a checkbox, instead it is invoked directly when the user clicks on an existing button on your site or can be invoked via a JavaScript API call. By default only the most suspicious traffic will be prompted to solve a captcha.
Once done with the configuration, click Save to save the changes or Cancel to discard them.
Please note that for the CAPTCHA service to enter into effect, you must turn on using the toggle on the top right corner of the screen.
Suspicious IP Throttling Service
Suspicious IP Throttling Service will protect the application against suspicious logins targeting too many accounts from a single IP address. The service uses the velocity of login attempts from an IP for any number of accounts against an application as a risk signal. It detects when a bot/script tries too many username/password combinations within a short period of time.
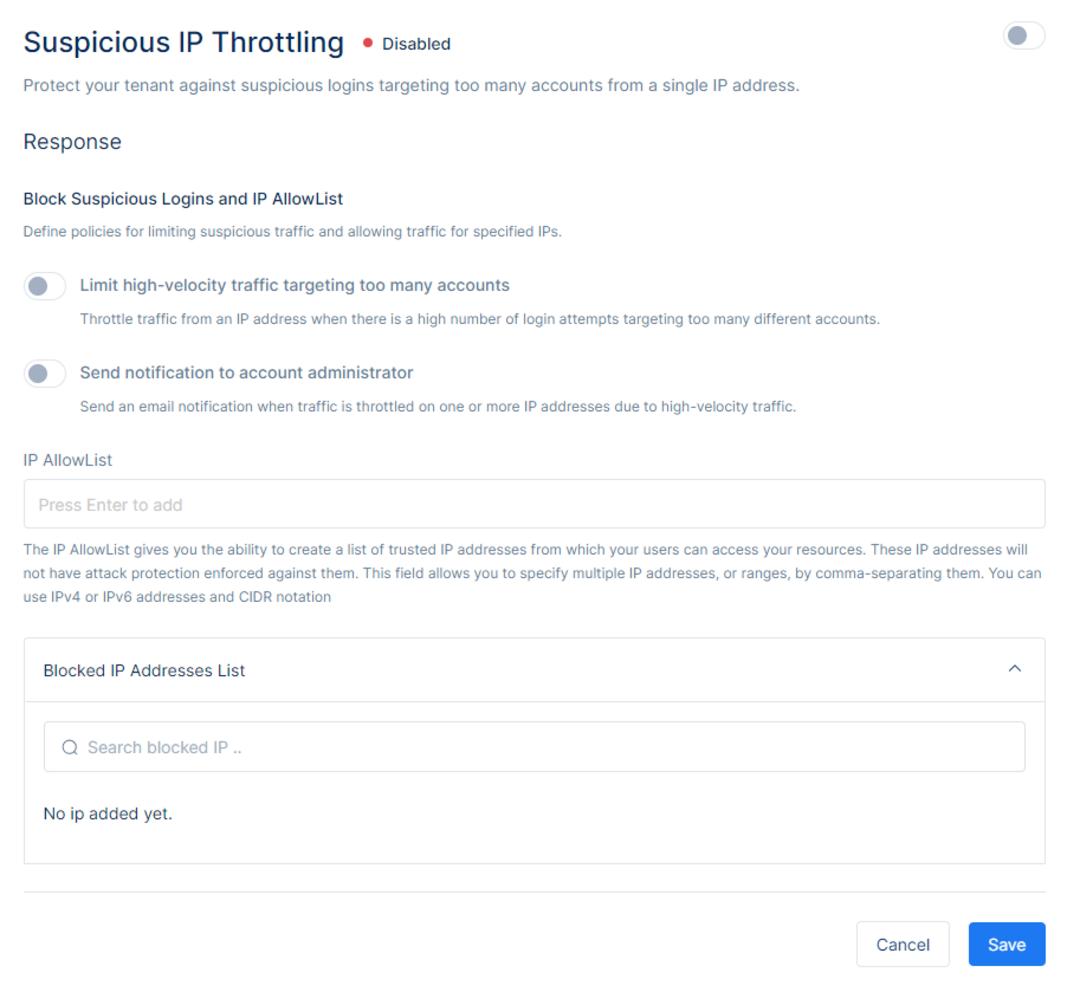
On the Suspicious IP Throttling Service page one will be able to define the policies for limiting suspicious traffic for specific IPs.
Limit high-velocity traffic targeting too many accounts will throttle traffic from an IP Address when there is a high number of login attempts targeting too many different accounts. When toggled, upon detection of a high number of consecutive signup attempts or failed login attempts from an IP address, Porta will suspend further attempts from that IP address.
Send a notification to the account administrator when traffic is throttled on one or more IP addresses due to high-velocity traffic. The Porta administrator will receive an email notifying them that an IP address has been throttled due to a high number of login and/or signup attempts targeting too many accounts. A report can be found under the Monitoring section in the Porta Dashboard.
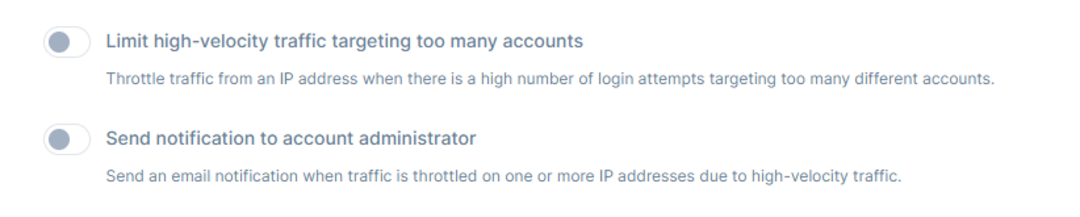
The IP AllowList provides the option to create a list of trusted IP Addresses from which the users can access the resources but be informed that these IP Addresses will not have attack protection enforced against them. For example, if certain testing is being performed under a single IP address, one can add that IP address to the IP AllowList in order to prevent throttling of traffic due to high-velocity.
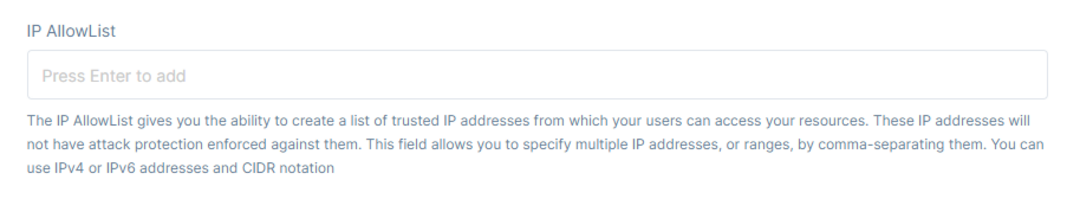
Below the AllowList, one can view the Blocked IP Addresses List. The list outlines the IP Addresses that are blocked informing the administrator from which IPs users are not able to login. To allow logins and/or sign up attempts from the IP, the administrator must remove that IP from the Blocked IP Addresses List first or the IP address will be unblocked automatically 15 minutes after being blocked.
Brute-force Protection
Brute-force Protection safeguards against brute force attacks that target a single user account.
On the Brute-force Protection Page, one can manage Login Thresholds by blocking suspicious traffic during end-user authentication. The administrator can set the maximum attempts for the number of consecutive failed login attempts from a single user before the user is blocked. Upon reaching this threshold of failed login attempts the user will be notified that they have had too many failed attempts and must contact the administrator to unblock their account.
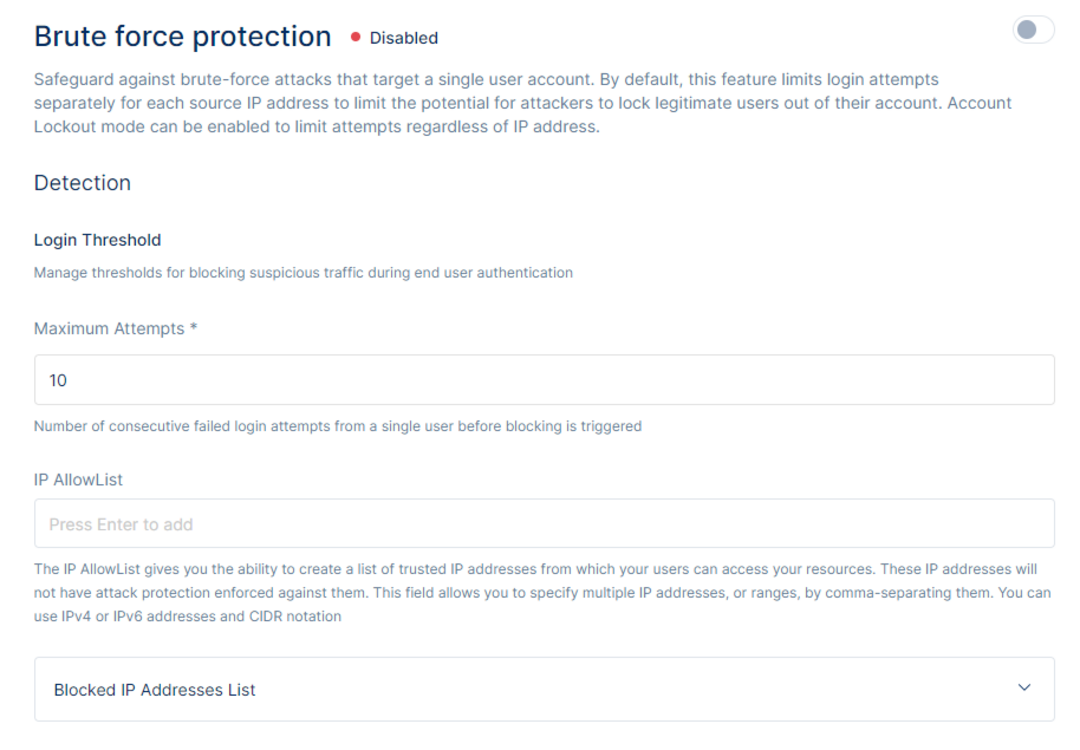
The IP AllowList allows administrators to create a list of trusted IP addresses. Once an IP address is added to the list, brute-force protection is not enforced against the specified IP addresses.The maximum threshold of login/signup attempts coming from that IP will not be executed and users will be able to try an unlimited number of login/sign ups even if their credentials are incorrect. This field allows you to specify multiple IP addresses, or ranges, by comma-separating them. You can use IPv4 or IPv6 addresses and CIDR notation.
Blocked IP Addresses List
The list outlines the IP Addresses that are blocked informing the administrator from which IPs users are not able to login due to a block executed as a result of login attempts that surpass the maximum threshold set by the administrator. To allow logins and/or sign up attempts from the IP, the administrator must remove that IP from the Blocked IP Addresses List first.
The Response section allows the administrator to control the policies on the security settings.
Setting the configuration for the Block Settings and enabling Block Brute-force Logins will block all the login attempts for a flagged user account for a particular Ip Address. Note their account will not be locked and if they are logged in on a different device they will still be able to access their account and profile.
Account Lockout will provide the ability to lockout an account regardless of IP Address when it detects numerous unsuccessful login attempts. This account will be blocked and can be unblocked by going to the respective user details and unblocking the account.
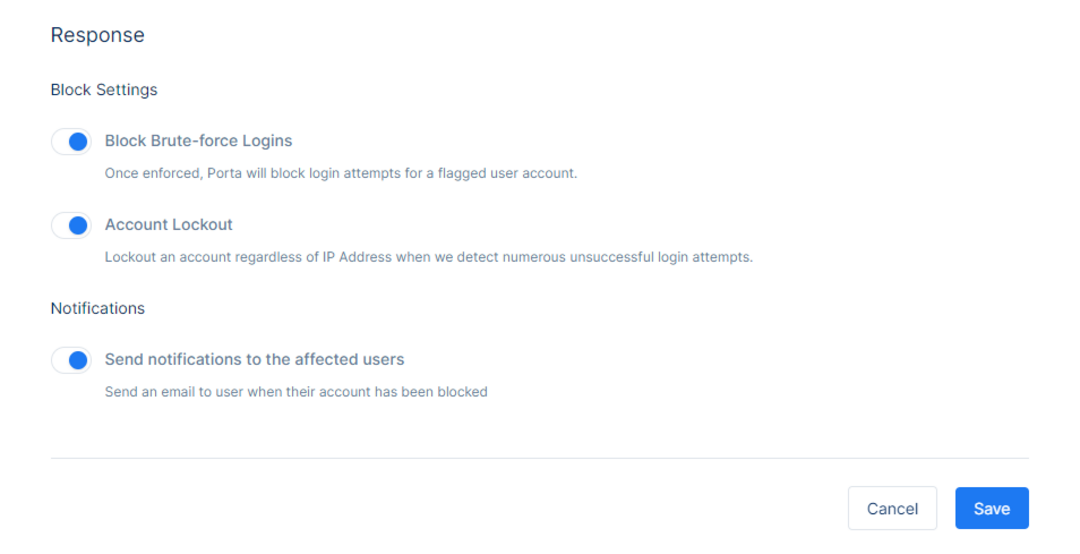
If ‘Send notifications to the affected users’ is toggled on, a notification email (“IP address blocked” in SmartEmailing configuration) is sent to the user in their email address notifying them that the IP address in which multiple failed login attempts have been made has been blocked. The user will have to either contact the administrator to remove said IP from the blocked list or login through a different IP address.
Please note that to enforce brute-force protection one must toggle on the security setting on the top right of the screen and click Save. Otherwise, the settings are not saved and brute-force protection is not enforced.
Breached Password Detection
Porta can detect if a specific user’s credentials were included in a major public security breach and inform the users about the breached password.
When a user changes their password and sets the new password to a password that is classified as part of breach, Porta displays a modal on the registration page that informs the user that this password was part of a breach.
This security service can be enabled by using the toggle on the top right corner of the screen and clicking Save.
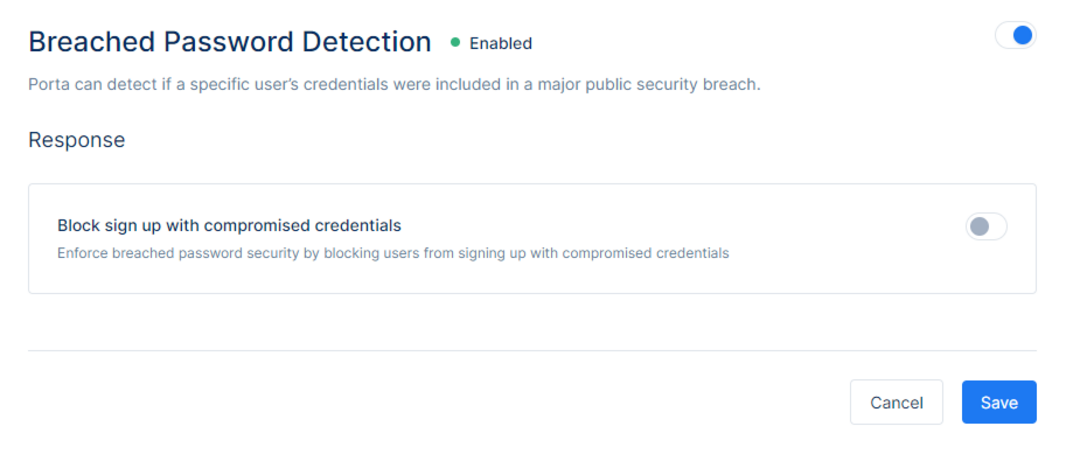
When Block sign up with compromised credentials is toggled on, Porta would enforce breached password security by blocking users from signing up with compromised credentials. If not toggled on, Porta will simply notify the user that they are attempting to sign up with a password that is classified as being part of a breach but allow them to continue the registration with compromised credentials.After the changes, make sure to click Save to save the changes or Cancel to discard them.
Multi-factor Authentication
Multi-factor Authentication works by requiring additional factors and steps during the login process to prevent unauthorized access. Porta offers three factors of multi-factor authentication including SMS, Email, and Authenticator App.
By SMS, the users will receive a text message containing a verification code. Please contact your Porta account representative to configure SMS multi-factor authentication.By Email, the users will receive an email message containing a verification code.
By Authenticator App, the users will secure access with a push notification using any authenticator app.
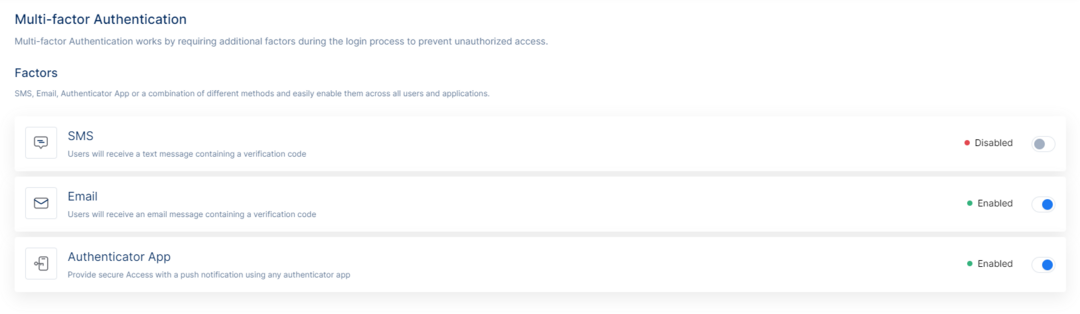
The options can be toggled on or off on the list view and no additional configuration is necessary, unless stated otherwise.
If a multi-factor authentication method is enabled, it becomes available to all users to use upon their discretion. If an enabled multi-factor authentication method is later disabled, all users, including users who have had it previously set-up, will have their MFA disabled and it will not be required during authentication. In addition, all users who previously had the method set up, will have to set it up again.
